Privacy/Proxy Services - a safe haven for cybercriminals?
By Alex Deacon
Key Findings
In this article, we wanted to understand the prevalence of privacy/proxy services associated with domain names listed on abuse block lists.
Key findings include:
- 88% of Abusively Registered Domain Names Have Unavailable Registration Information: Out of 414,218 unique domain names on abuse lists, 65% used privacy/proxy services, 22% had redacted registration information, and only 12% had registrant identity available.
- Privacy/Proxy usage is More Prevalent with Abusive Domains: Compared to a 2021 study of a representative sample of all domain name registration data, privacy/proxy services are much more prevalent for abusive domains (65% vs. 29.2%), while redacted registration usage is less prevalent (57.4% vs. 22%).
- Dominance of Major Registrars in Privacy/Proxy Services: The top two privacy/proxy services are affiliated with the largest registrars, GoDaddy and NameCheap. However, several smaller registrars and affiliated privacy/proxy services with a lower market share also had a notable proportion of abusive domains.
- An Accreditation Regime for Privacy/Proxy Services is Necessary: Our research findings indicate that an effective accreditation regime for privacy and proxy service providers is still needed. This policy should clarify when and how the terms ‘privacy’ and ‘proxy’ are used to minimize confusion. It should also ensure that collection and disclosure obligations are consistent across privacy/proxy providers to ensure compliance with the European Union NIS2 Directive.
- RDAP Compliance Must be Improved: We observed several compliance issues with the Registration Data Access Protocol (RDAP), including improperly formatted responses, non-compliant JSON responses, and unresponsive/unavailable RDAP servers. As such, ICANN should continue to require the support of Port 43 WHOIS until it has ensured that all Registrars and Registries' RDAP implementations fully comply with the ICANN policies and RDAP Technical Profiles.
Introduction
The Domain Name Registration Data Directory Services, commonly known as the WHOIS system, has been a fundamental component of Internet infrastructure since the 1980s. Over the years, WHOIS has adapted to address privacy concerns and comply with global privacy regulations. In the late 1990s and early 2000s, domain registrars introduced Privacy/Proxy services to protect the personal information of domain name registrants by replacing their contact details with those of the privacy/proxy service provider in the public WHOIS database. In addition to addressing privacy concerns, privacy/proxy services are also used to minimize spam, reduce identity theft, avoid harassment and stalking, protect against cyber attacks, and many other legitimate uses.
The primary goal of our analysis was to understand the prevalence of privacy/proxy services associated with domain names that appeared on abuse block lists by analyzing and then classifying the related domain name registration information into one of three categories.
- Privacy/Proxy Service Detected
● Registration information associated with the domain name indicates a privacy/proxy service was used. - Redacted Registration Information Detected
● Registration information associated with the domain name indicates that the registration data has been redacted for privacy purposes, as ICANN policy allows. Redacted registration data typically substitutes the string “Redacted for Privacy” (or similar) for the registrant’s data. - Registrant Identity Available
● Registration information associated with the domain name indicates the registrant's information is available. This means that the information is 1) not using a privacy/proxy service and 2) has not been redacted.
Using the DNS Research Federation's DAP.LIVE system, we defined a methodology to detect these categories (See Appendix A for details). The abusive domains were found on the following abuse lists:
- Phishing: , OpenPhish, APWG Phish
- Malware: URLHaus, Malware Patrol
- Spam: Spamhaus
The domain names' registration data was obtained via the DAP's internal RDAP implementation or using WHOIS when RDAP is not supported or available. Three months of data, starting on March 1, 2024, and ending on May 31, 2024, were analyzed for this article. Finally, we did not determine or distinguish Privacy services from Proxy services; thus, they are collectively referred to as privacy/proxy services.
Findings
Registration information for 88% of abusively registered domain names is unavailable
The number of unique domain names that appeared on the abuse lists for the period in question and for which we obtained registration data from the Registrar directly was 414,218. Using the methodology described in Appendix A, we found that the ratio of registrations using Privacy/Proxy vs. Redacted vs. Registrant Identity Available was as follows.
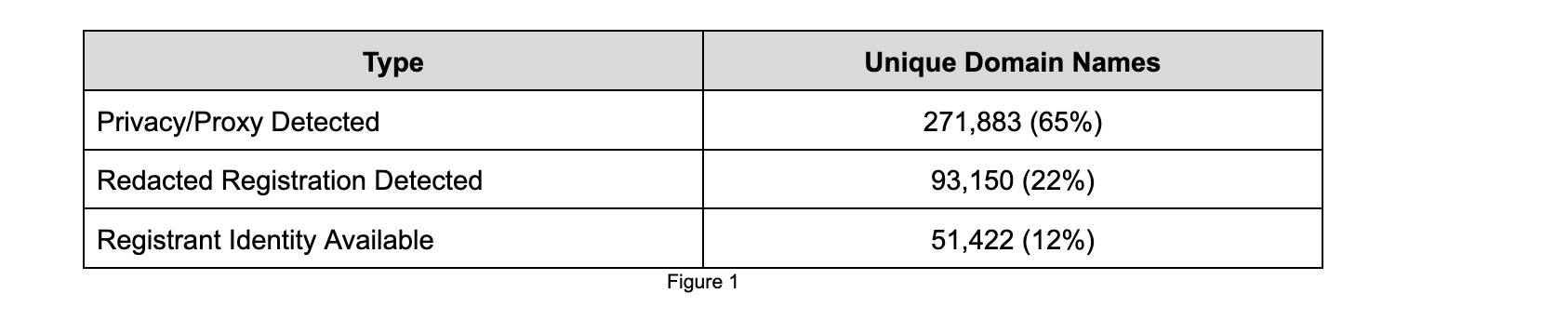
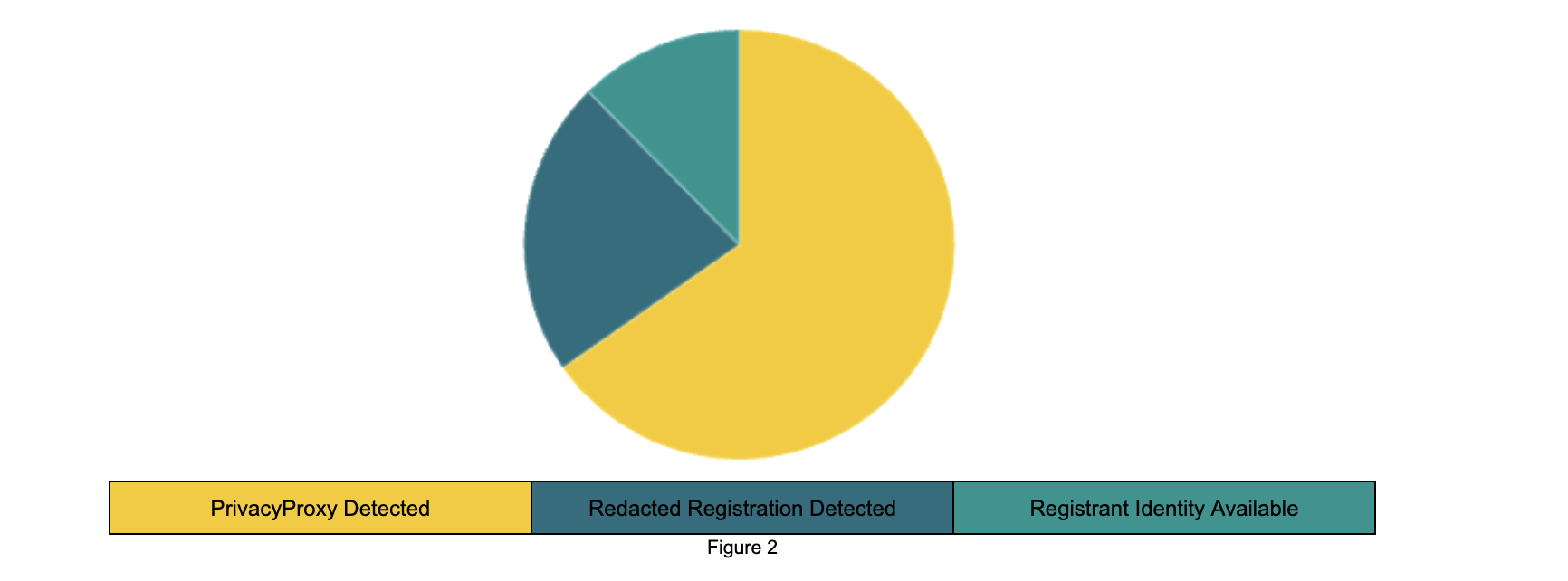
The results show that privacy/proxy services and redaction are heavily used for abusive domain names. This means that 88% of registration data for these abusive domain names is not directly available.
We were curious how this ratio compares with a general sample of registered domain names, e.g., domain names not identified as abusive. Interisle's “WHOIS Contact Data Availability and Registrant Classification Study,” published in January 2021, contains the following details.
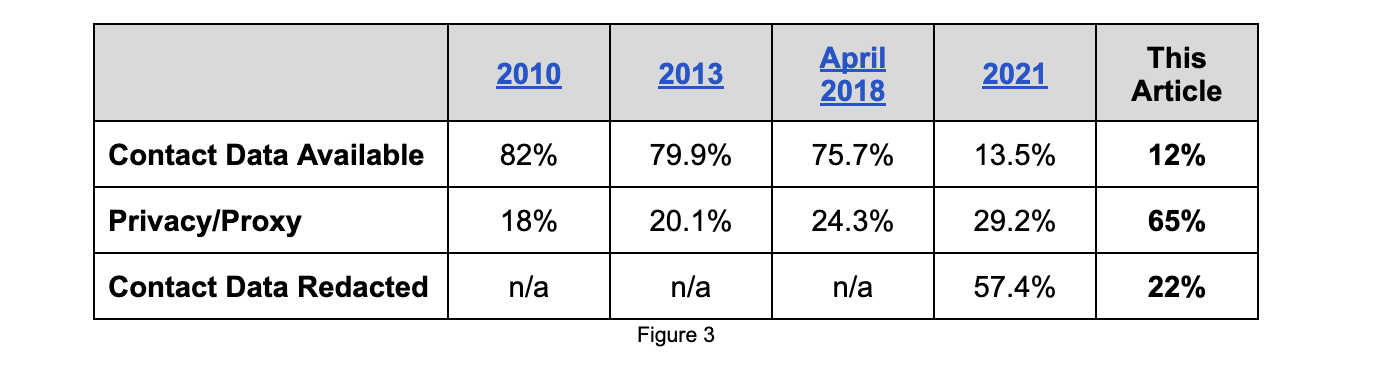
Comparing our findings of abusive domains with the results of the 2021 Interisle Study, we see that the percentage of registrations where contact data is available (i.e., Registrant Identity Available) is very close (only 1.5% lower) to the 12% we detected. However, registrations using privacy/proxy services are more prevalent than those with redacted information, with privacy/proxy usage at 65% and redacted registrations at 22%. One of the reasons for this is the announcements from several large registrars, including GoDaddy, that they have implemented a blanket proxy protection for all registrations.
Registrations where privacy/proxy services were detected
When we examine the privacy/proxy services in use, it appears they are all owned by a registrar. Very few domains are protected by a third-party provider not associated with the domain’s sponsoring registrar. Table 4 lists the top 10 privacy/proxy services detected and the associated sponsoring registrar.
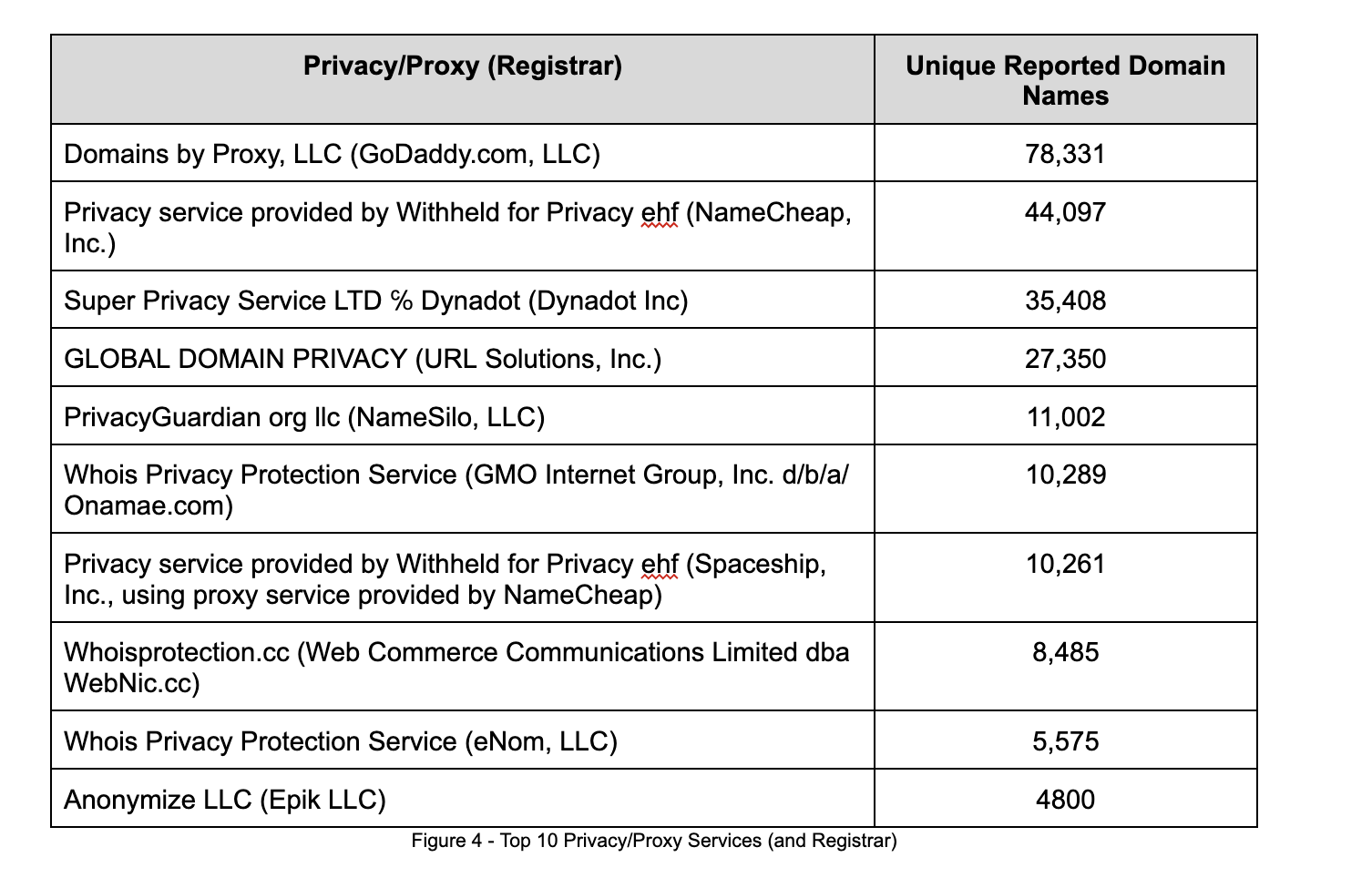
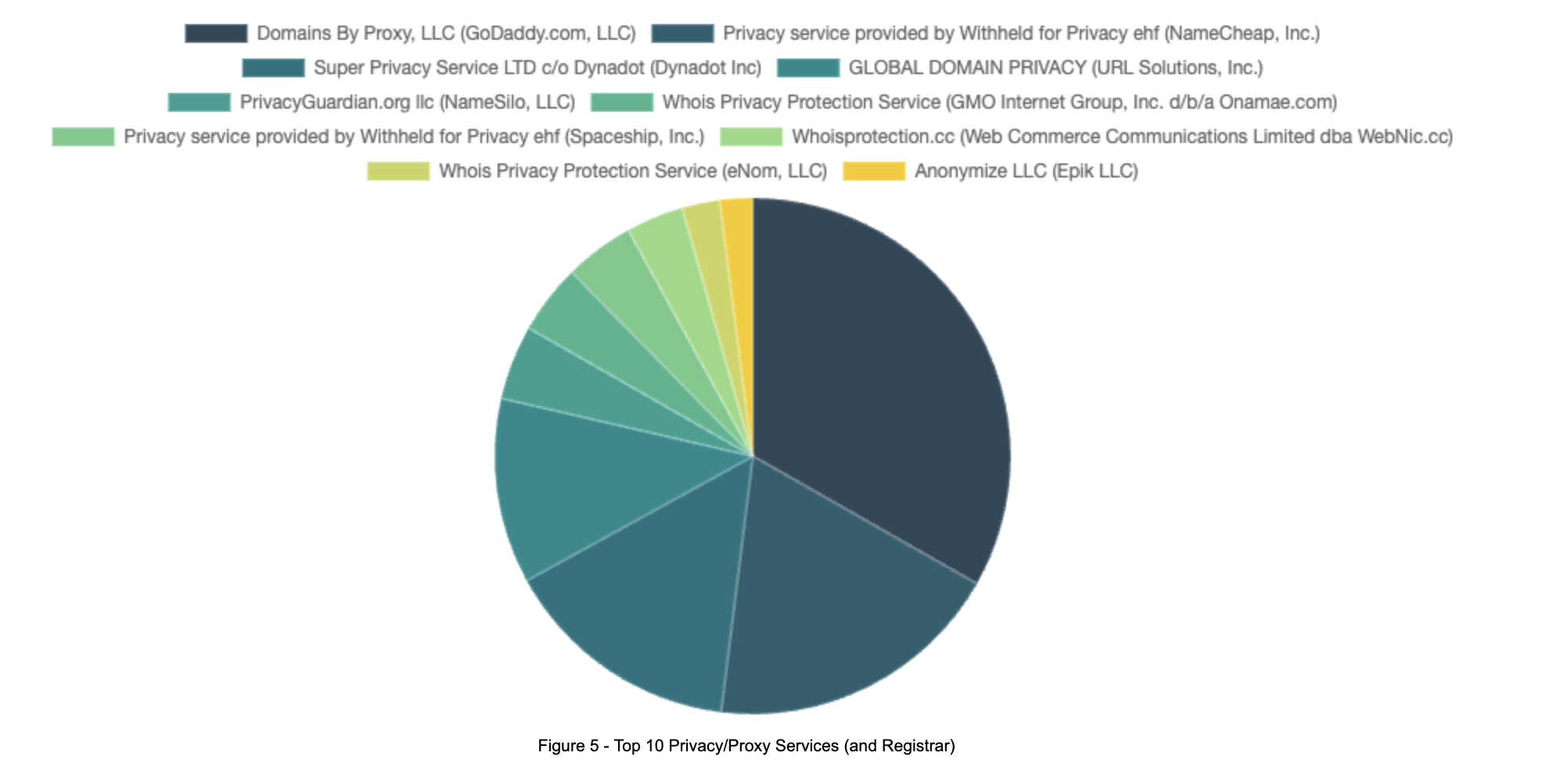
Unsurprisingly, the top two privacy/proxy services are affiliated with the largest registrars: GoDaddy and NameCheap. However, several of the top 10 privacy/proxy services are associated with registrars with a much lower market share, yet apparently, a more significant proportion of abusive domains in our data set.
Registrations with redacted registration information
Per ICANN policy, domain name registration can be redacted by simply substituting a string similar or equivalent to “Redacted for Privacy.” The policy allows all registrant data fields to be redacted in this manner, except the “Registrant State” or “Registrant Country.” Our analysis determined that 22% of registrations associated with abusive domain names are redacted via this method.
Looking more closely at the registration data associated with the domain names in this category, we found compliance issues with some returned data.
First, several registrars [1] are redacting one or more of the following data fields: Registrant State, Registrant Country. The redaction of these fields is prohibited per the ICANN Temp Spec Policy and the newly published Registration Data Specification.
Second, several registrars [2] also redact the Registrant Email field. While the registrar can publish an anonymized email address or link to a web form, both policies also prohibit redaction of the Registrant Email field using the term “Redacted” or similar. The redaction of this field makes it impossible for third parties to contact the owner of the domain name in an attempt to resolve technical, legal, or any other issues found with the associated domain name. Without a means to communicate with the domain name's owner, third parties are forced to involve the registrar (or reseller). This situation should be avoided whenever possible.
Finally, we observed registrations in this category publish a Registrant Organization value. While this is permitted by the policy with the registrant's consent, we find instances where the name of the sponsoring registrar has been placed in this field. For these cases, Section 6.6.2 of the Registration Data Specification specifies that the registrar is the registered name holder. However, we don’t believe this indicates the use of a privacy/proxy service. If this were the case, the full registration data of the privacy/proxy service should also be published. So, depending on the intent, this may or may not be a compliance issue.
Registrations where registrant identity is available
The last category represents domain name registrations for which the registrant identity is available in the WHOIS system. This means that neither a privacy/proxy nor redaction has been applied. Our analysis calculated that 12% of the domain names in our data set were represented in this category.
We did not validate or verify the data in this category. However, a manual analysis shows instances where the data is clearly inaccurate. For example, Registrations where
- the Registrant Name is ‘aaaaaaa’ or a string that has been randomly generated
- the same Registrant Name is used for many different registrations (e.g. “ZHADAN ZHADAN” or “DUOWANG DUOWANG” or “YULEI YULEI” or “sili sili.”) along with address, city, and state information that might be valid, but look suspicious.
The implementation of the European Union NIS2 Directive should improve the accuracy of domain name registration information because its requirements for complete, accurate, and verified data apply to registrars and registries as well as to privacy and proxy service providers.
An accreditation regime for privacy/proxy services is necessary
Recently, ICANN announced it would resume work on privacy proxy policy after an unfortunate 6-year pause in implementation. As a participant in the original Privacy/Proxy Services Accreditation Issues (PPSAI) work, I believe the time and effort put into the policy and the nearly completed implementation should be leveraged and reused as applicable, not discarded. The fundamentals of this policy, which was unanimously approved by the GNSO council and ratified by the ICANN board, and its subsequent implementation can be used as a foundation for an effective privacy/proxy policy, even in a post-GDPR world. Specifically, I would like to see policies to address the following issues -
- Creation of an accreditation regime for privacy and proxy service providers. This will move currently “unregulated” privacy/proxy services into the purview of ICANN compliance, ensuring that disclosure obligations are the same for privacy/proxy providers as they are for registrars.
- The specification of an RDAP flag that indicates if a privacy or proxy service is in use would address the difficulties in identifying such services. In addition, it would clearly indicate who the registered name holder of a domain name is and which service provider is best able to handle requests for registration data.
- We observed that service providers use the terms privacy and proxy interchangeably, which could lead to confusion. Specifically, we found that several services use the term “Privacy” in their name but are actually proxy services. An approved ICANN policy could clarify how and when these terms should be used, as the distinction between privacy and proxy services is legally significant. The proxy provider becomes the registrant for proxy registrations and assumes responsibility for the domain name's use or abuse (unless they disclose the identity and contact information of the customer under RAA Section 3.7.7.3). Whereas a privacy registration is just there to shield the registrant's contact information (rather than their identity), who remains legally responsible for the domain name and its use.
Longitudinal analysis
While the data above focused on domain names found on abuse lists between March 1, 2024, and May 31, 2024, we wanted to see how the use of privacy/proxy services trended over time. To do this, we created a live interactive dashboard that can be viewed at this link.
This dashboard contains the privacy/proxy detection analysis results for domain names reported to abuse blocklists for the previous 7 days. Using the methodology described below in Appendix A, we analyze the registration information associated with each domain name to determine if a Privacy/Proxy service has been detected. Categorizing the registration into the three categories referenced earlier in this article.
The dashboard contains visualizations charting the 7-day rolling average of these categories. In addition, it contains tables listing the unique domain names and registration data found for each category. The data in these tables can be searched and filtered using the parameters at the top of the page.
RDAP compliance must be improved
Getting reliable and timely access to timely registration information is critical to the analysis we undertook in this article. As mentioned earlier, our primary method for obtaining domain name registration data is via the new RDAP protocol. The Registration Data Access Protocol (RDAP) is considered better than the WHOIS protocol primarily due to its enhanced features, security, and compliance with modern internet standards, including structured and machine-readable data, making it easier for automated systems to parse and process.
Unfortunately, our experience with RDAP related to this project indicates that more work is required to bring RDAP response into parity with the “historical” WHOIS protocol responses. I encountered multiple compliance issues, which would be an interesting topic for future articles. But in summary, they included challenges such as -
- Improperly formatted and insufficient JSON responses (not compliant with the ICANN RDAP profiles).
- JSON responses contain completely different data than those received via the WHOIS protocol.
- In some cases, data returned from the Registrar did not match data returned from the Registry. The Registry's further redaction of registrant data was the main reason for this, yet there exist responses where the data returned from the registry and registrar were not similar at all.
- Non-responsive (and perhaps misconfigured) RDAP servers
- Performing RDAP queries at scale often results in the RDAP server throttling queries. While I appreciate the need for throttling from a service availability point of view, I believe more can be done to minimize throttling for legitimate purposes.
The transition to RDAP was supposed to result in easier implementations and more accurate responses that are easier to parse and understand. However, it is clear that this promise has yet to be fulfilled, and the complexities of managing “edge cases” and handling of malformed or buggy RDAP responses continue to complicate RDAP implementation. Because of this, ICANN should continue to require the support of Port 43 WHOIS until it has ensured that all Registrars and Registries' RDAP implementations fully comply with the ICANN policies and RDAP Technical Profiles.
Conclusion
Our analysis reveals a significant trend in the use of privacy/proxy services and redaction in domain name registration data, particularly among those associated with abusive activities. With 88% of registration data for abusive domains being either protected by privacy/proxy services or redacted, it becomes evident that there is a substantial reliance on these services. This trend contrasts sharply with general domain registration practices observed in previous studies, indicating a growing preference for privacy among malicious actors. The increased use of privacy/proxy services, especially by major registrars like GoDaddy and NameCheap, highlights the need for robust policies and regulations to ensure transparency and accountability in domain name registrations.
Additionally, our study underscores several compliance issues with the current implementation of the Registration Data Access Protocol (RDAP). While RDAP promises improved access to registration data, our findings show that it falls short in several areas, including data accuracy and server responsiveness. These challenges highlight ICANN's need to ensure strict compliance with RDAP specifications before retiring the historic Port 43 WHOIS protocols. Moving forward, it is crucial for the domain registration ecosystem to address these gaps and enhance the reliability and transparency of registration data, particularly to curb the misuse of domains for malicious purposes.
Acknowledgments
Thanks to Greg Aaron for his helpful input, review, and guidance.
References
- Interisle: WHOIS Contact Data Availability Study
● https://interisle.net/insights/contactstudy2021 - NORC, University of Chicago: ICANN Study on the Prevalence of Domain Names Registered using a Privacy or Proxy Service among the top 5 gTLDs
● https://www.icann.org/en/system/files/newsletters/privacyproxy-registration-services-study-14sep10-en.pdf - NORC, University of Chicago: WHOIS Registrant Identification Study
● https://gnso.icann.org/sites/default/files/filefield_39861/registrant-identification-summary-23may13-en.pdf - ICANN: Registration Data Services Policy
● https://www.icann.org/resources/pages/registration-data-policy-2024-02-21-en - ICANN: Registrar Accreditation Agreement
● https://www.icann.org/en/system/files/files/registrar-accreditation-agreement-21jan24-en.html
Appendix A: Methodology
- The domain names we analyzed were added to the following security block lists for the time specified. Entries not using a domain name (e.g. IP address) were removed from the data set.
● Phishing: Phishlabs, APWG Phish
● Malware: URLHaus, Malware Patrol
● Spam: Spamhaus - For each domain name appearing on these lists, the DAP attempted to obtain the associated registration data as soon as possible using the RDAP protocol (or WHOIS when necessary). Domain names where we could not obtain reliable registration data from the registrar were discarded from the data set.
- To kick-start identifying privacy/proxy services, we manually analyzed a subset of domain names and looked for the strings “privacy” and “proxy” in both the registrant name and registrant organization fields. This resulted in a list of known privacy/proxy services and associated registrant registration data
- Using this list and the registration data associated with each privacy/proxy service, we could determine which domain names used one of the known privacy/proxy services. The list was added to and refined as we processed more data over time.
- Using the remaining data set, we determined which registrations were redacted by searching for the use of redacted terms (and their equivalents) in the registrant data fields.
- Domain names not found using a privacy/proxy service or containing redacted registration data were classified as domain names where the registrant identity was available. Periodically, we manually review this list to determine if further refinement of the privacy/proxy or redacted queries is required.
_____________________________________________________________________________
[1] The following is a sample of registrars where we detected redacted state and country data in RDAP responses. This is not an exhaustive list.
- Xin Net Technology Corporation (possible non-compliant RDAP)
- Chengdu West Dimension Digital Technology Co., Ltd.
- Jiangsu Bangning Science & technology Co. Ltd.
- Shanghai Meicheng Technology Information Development Co., Ltd.
- DNSPod, Inc. (possible non-compliant RDAP)
[2] The following is a sample of registrars where we detected redacted email/contact information in RDAP responses. This is not an exhaustive list.
- Hong Kong Juming Network Technology Co., Ltd.
- Chengdu West Dimension Digital Technology Co., Ltd.
- Hefei Juming Network Technology Co., Ltd
- Xin Net Technology Corporation
- Hongkong Kouming International Limited



