The DNS and cybercrime: NIS2 to the rescue
By Georgia Osborn
On 10 November 2022, the DNS Research Federation hosted a roundtable discussion in Brussels, bringing together representatives from government–including the European Commission and UK–private sector, civil society, academia and civil society experts. The event was held under the Chatham House Rule.
The contested role of domains in cybercrime
Everything that happens online relies on the domain name system (DNS) and IP addressing to some extent. Yet, the connections between the DNS and today’s cyber policy challenges, such as cybercrime, are sometimes missed. The discussions highlighted the difficulties surrounding DNS abuse and its contested role in cybercrime as well as the upcoming NIS2 Directive, the final text of which was published on the same day as the roundtable event.
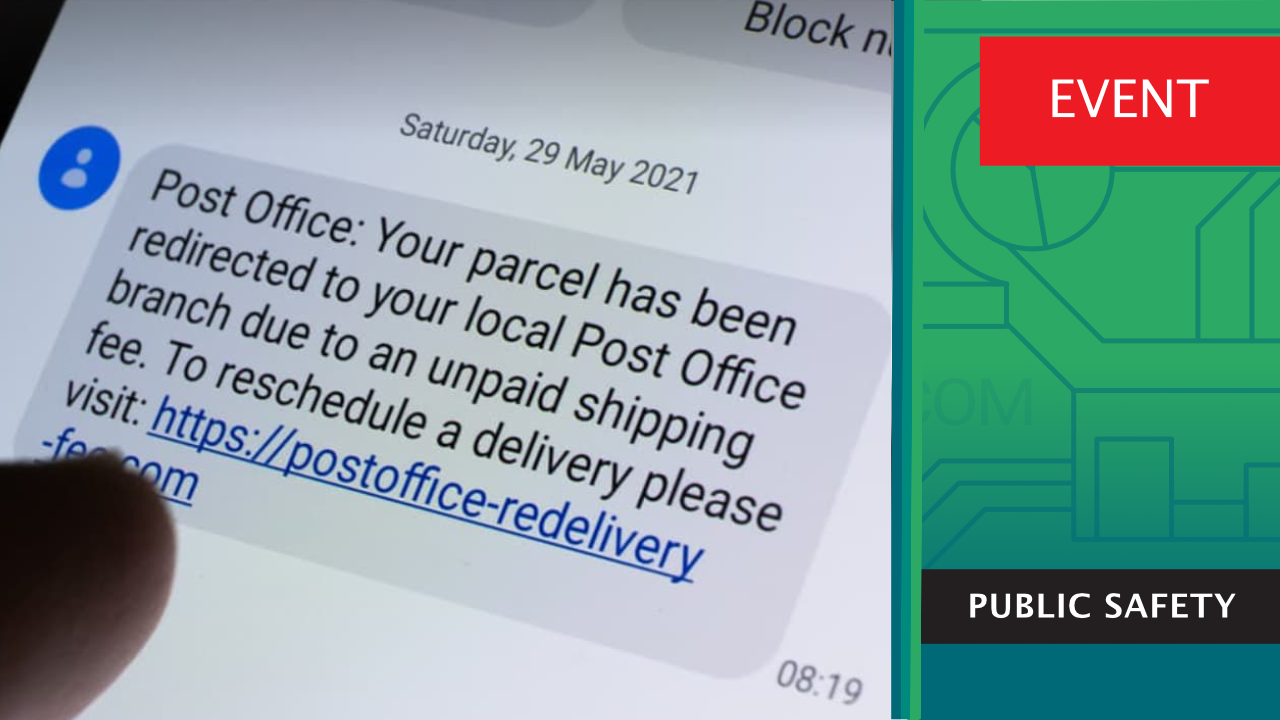
The first session opened with an introduction of the problem of DNS abuse and the critical role it plays to the success of cybercriminals. There is a lack of commonly agreed definitions and metrics for DNS abuse. Different definitions and methodologies for measuring DNS abuse, and yield varying results.
The changing nature of cybercrime and the contested role of DNS reveals the tension between public good and commercial value as the multistakeholder community have different positions. There can be a lack of clarity as to which stakeholders hold responsibility for combatting DNS abuse–commercial industry, ICANN, IETF or law enforcement. Diverse stakeholders offer contrasting approaches to the issue, and breaking down a problem into smaller pieces can make it easier.
Data is essential - different methodology, different answer
The roundtable participants highlighted the importance of the availability and transparency of data, and the essential need for frictionless data sharing across borders. Many of the problems discussed around DNS abuse are human problems. DNS abuse is one of the many aspects of cybercrime which all face a similar problem in terms of cross-border data sharing across the world around liberal democracies and non-democratic countries.
The question of who runs the Internet is a running question as no one has sole responsibility. Therefore the diversity of multistakeholder approaches is even more important. We can agree we need to try to make it harder for the criminals, yet the methodologies and different approaches to it can be competing. Different data tells different stories. We may never get to a point of no DNS abuse or zero DNS abuse, so what is an acceptable amount and what should we be aiming towards?
Focus on consumer harms
The definition of DNS abuse has been contested and the role of this session is not to define DNS abuse, Instead, the focus is on the real harm that is caused to individuals. Understanding the different methodologies in measurement of DNS abuse can be a first step. Research commissioned by the DNS Research Federation for the roundtable focused on qualitative experience of 5,000 consumers as the victims of domain-related scams. The research showed that 92% of consumers have received an online scam in an email or text message with a link including a brand name. More than half feel that the frequency of receiving such scams has increased, and more than one third receive an email or text with links more than once a week. Consumer research conducted on behalf of the Global Anti-Scam Alliance on 3,400 participants had similar findings, with 73% exposed to a scam in the past year, and 48% saying they fell for a scam.
This diversity of approaches in fighting cybercrime is positive and each stakeholder can make important contributions to this space. Multistakeholder conversations such as this session are critical in the fight against DNS related cybercrime.
Impact of regulation
Having explored the dimensions of the role of the DNS in cybercrime and contrasting approaches to measuring the problem, the second session examined the benefits and risks of proposed EU regulation in this area. There can easily be a sense that the discourse has become stuck, and several participants expressed frustration at the perceived impasse. Throughout the different stages in history of fighting DNS abuse, whether that be through the access to the public WHOIS system and now the NIS2 Directive, the aim remains the same; to balance the importance of data protection and privacy with public safety and security.
The solutions to some of the issues surrounding DNS abuse including the NIS2 Directive have wider implications such as e-IDs and Alternative Naming Systems. The NIS2 Directive makes DNS security essential. The variety of practices within this space may not be a weakness, but a strength. The fact there is such a variety of methodologies can help understand this problem and fight DNS abuse from different perspectives.
The NIS2 Directive, approved on 10th November 2022 coinciding with this session was discussed at length and the issue of data validation and data verification was highlighted. There is an importance of making a distinction between the two. At present, the implementation of technological solutions such as e-IDs is not consistent across all EU member states and therefore are not ready for cross-border validation or verification across the entire EU. Some participants noted that the EU institutional approach of working in silos may suggest that security and privacy cannot co-exist peacefully and can create confusion for those who have to implement the Directive. Differences in national implementation of the Directive may lead to a patchwork of inconsistent approaches across the Union. It remains to be seen how potential inconsistencies in national approaches will interact with the NIS2’s extraterritorial effect - will there be a race to the bottom, or a race to the top, with the strictest approaches posing a lower compliance risk for those outside the territory.
Participants at the roundtable emphasised the need not to duplicate rules or regulations that are already in practice. The DNS security community and other stakeholders already have many successful efforts that are working to curb DNS abuse, such as DNSSEC and others. Perhaps an unintended consequence of the raft of new regulations on technology is that they tend to affect those actors who are trying to do something about DNS abuse, without compelling bad actors to change their behaviour.
The sessions concluded with the importance of a multidisciplinary approach with the diversity of methodologies and solutions being critical as no one has sole responsibility for the Internet.
This blog represents the author’s own impressions of the conversations held at the round table sessions, and may not reflect the views and opinions of all participants.


