UDRP - An effective abuse mitigation tool?

By Alex Deacon
Summary
In the second part of our two-part series on Uniform Domain-Name Dispute-Resolution Policy (UDRP), we dive deeper into the UDRP data available in the DAP. While doing so, we discover instances where the UDRP was used to mitigate abuse, raising the question of what role the URDP should play in mitigating ever-evolving internet abuse and cyber threats. While there is evidence that the UDRP is being used to combat phishing and other attacks, the need for rapid response in such cases means that the UDRP - which takes on average 60 days - would have limited value unless combined with other mechanisms such as takedown or derouting of the domain name or associated content.
We start by looking at the prevalence of the top 100 most valuable brands referenced in UDRP decisions and found that 66 of those brands were represented. Also, 4,240 UDRP decisions referenced a domain name that contained a social engineering term. These terms, along with well-known brand names, are often used to launch attacks against internet users.
To get a more concrete view of the intersection between domain names in UDRP decisions and those reported to well-known abuse block lists, we discovered that 705 cited domain names overlap with these lists. Notably, most of the URLs reported used domain names that employed homoglyphs to impersonate well-known internet brands. Finally, we calculate that the average decision length of approximately two months raises the question of whether UDRP is a timely and appropriate tool for mitigating domains actively used for abuse.
Diving Deeper into the DAP UDRP data
In my previous article, Domain Name Disputes: large scale text analysis tells the UDRP story, I introduced the UDRP data set available on the DNS Research Federations DAP.LIVE platform and provided a high-level overview highlighting details on UDRP providers, the number of cases filed per year, the organizations that filed UDRPs (complainants), and the decision outcomes. For this article, I wanted to dive deeper into the UDRP data to demonstrate what additional insights we can glean from the UDRP data and what exciting analysis we can perform by leveraging both project-specific data imported into the DAP in conjunction with existing DAP data sources.
Brands and Social Engineering Terms
In the first part of this series on UDRP data, I analyzed the organizations (a.k.a. complainants) that filed UDRP cases and touched upon how a single URDP case may list one or more domain names within it. For this article, I wanted to look at the individual domain names present in those cases to understand how many of the top 100 most valuable brands appeared in those domain names. Like previous blogs - Blog: Brand Names in Blockchain Domains: New Frontier for Brand Owners and Blog: Bait and switch - how social engineering terms combine with brand domains to lure users into online scams - I imported the Top 100 Brands by Brand Value for 2023, as reported by Visual Capitalist, into a local project-specific data set for my analysis.
By joining that brand data with the set of domain names associated with UDRP decisions available on the DAP, we find that 66 (66%) of the top 100 brands are represented.

Figure 1 - Number of Domain Names by Top 100 Brand
Figure 1 (above) visualizes the number of domain names found in UDRP decisions by brand. We see “the usual suspects” at the top of this list: Google, Facebook, Instagram, and Amazon, followed by many other well-known consumer brands. Note: I removed the brands EY (Ernst & Young) and TD (now owned by Charles Schwab) as they are common combinations of letters often found in domain names.
A total of 7,250 UDRP decisions had a domain name that contained a top 100 brand. That represents 9% of the 84,630 decisions in our data set.
Next, I was curious to understand how many domain names referenced in UDRP cases in our dataset contained “social engineering terms.” As we discussed in Blog: Bait and switch - how social engineering terms combine with brand domains to lure users into online scams, social engineering terms are words included in domain names often used by scammers and attackers to “lure” users into clicking on them.
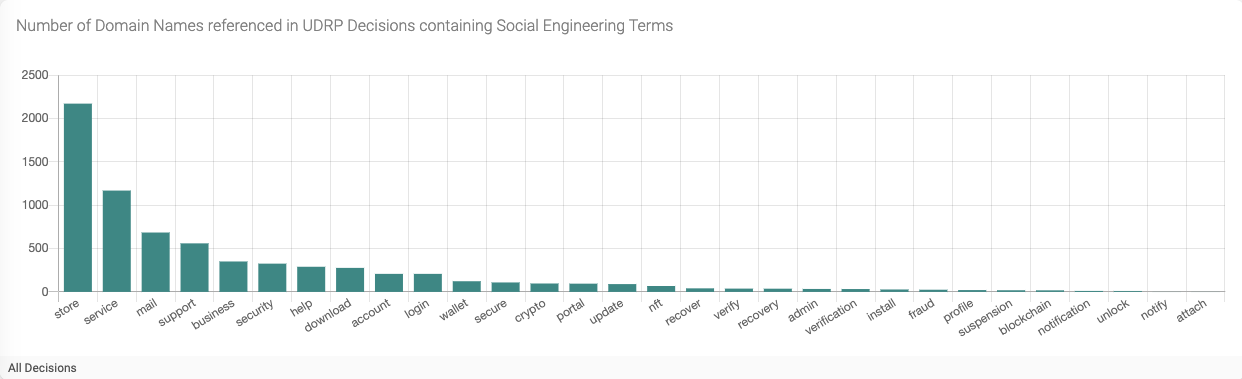
Figure 2 - Number of Domain Names by Social Engineering Term
The results showed that all 30 social engineering terms in our local data set were found in domain names associated with UDRP decisions. (Figure 2) The strings store, service, mail, and support top the list with 4,596 domain names between them. Overall, 4,240 UDRP decisions referenced a domain name that contained a social engineering term. That represents 5% of the 84,630 decisions in our data set.
While the percentage of domain names that include brands and social engineering terms is relatively low, I still found it interesting, as it indicates the UDRP is being used to mitigate abuse related to spam, malware, and phishing in certain circumstances.
Because successful UDRP filings result in the domain name being transferred from the respondent to the complainant, one could argue that using UDRP is the “safest” way to mitigate abusive domains, as there is no way they can be re-registered by new registrants for abuse purposes in the future. However, it raises interesting questions about whether UDRP is an appropriate tool for mitigating abuse, especially given how long a typical decision takes. We will further analyze and investigate this later in this article.
Limited Overlap with Domain Name Abuse Block Lists
Using the DAP, we can better understand how the UDRP is used to mitigate specific types of abuse and how often. This is accomplished by checking the abuse lists available on the DAP to determine how many domain names found in UDRP decisions are also found on these lists. For this analysis, we used data from the following abuse lists:
- Malware Combined: Source URLhaus
- Phishing Combined: Source OpenPhish and APWG
- Spam: Source Spamhaus
Our analysis found that 705 domain names cited in UDRP decisions were also found on one or more abuse block lists. This represents a very small 0.4% of the 159,045 unique domain names cited. However, despite the low percentage, looking at the domain names that overlap these lists is quite interesting.
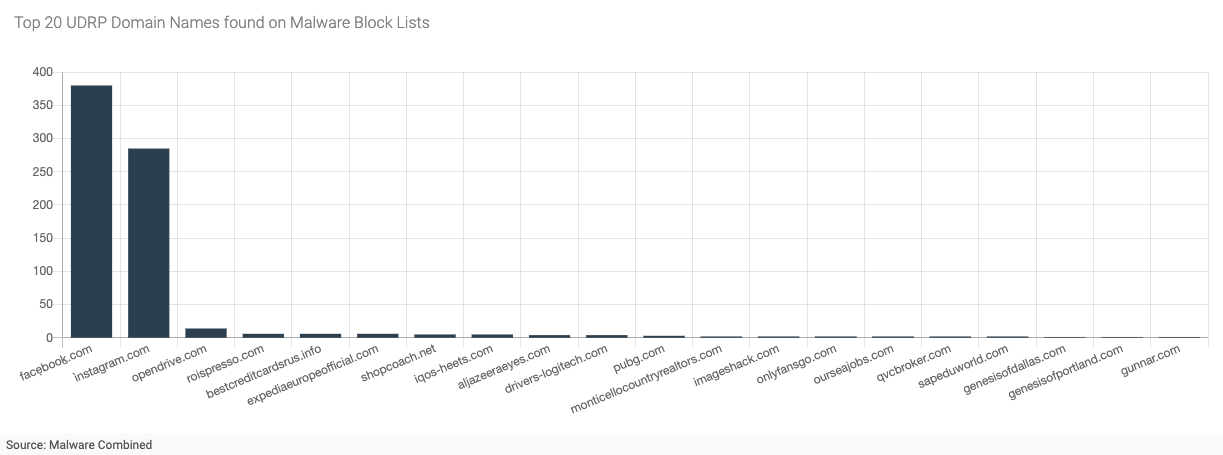
Figure 3 - Top 20 Domain Names Found on Malware Block Lists
Figure 3 (above) shows the top 20 domain names (out of 41) found also in the Malware Combined data set. The numbers on the y-axis represent the number of reported URLs reported to the abuse vendors that contained this domain name. The domain name facẹbooḵ[dot]com, which uses the two non-ASCII characters ẹ and ḵ (a.k.a. homoglyphs), was reported to have been used in 380 distinct malware URLs. Similarly, the domain name Ìnstagram[dot]com, which uses an accented Ì, was reported to have been used in 285 distinct malware URLs. Domains containing brands owned by Meta Platforms, Inc. represented 88% of all malware URLs reported to URLhaus and 7% of all overlapping domains.
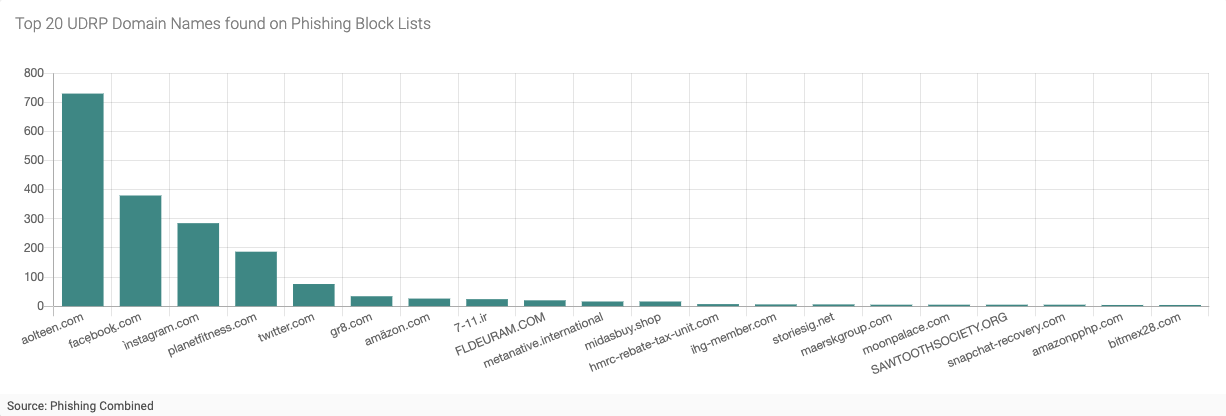
Figure 4 - Top 20 UDRP Domain Names Found on Phishing Block Lists
Figure 4 (above) shows the top 20 domain names (out of 269) found also in the Phishing Combined data set. Again, we see the two Meta Platforms Inc. branded domain names facẹbooḵ[dot]com and Ìnstagram[dot]com near the top of the list, indicating that these domains were used for large malware and phishing attacks at some point. At the top of the list is aolteen[dot]com, with 730 distinct phishing URLs reported. Finally, looking further down this list, we see several additional domain names using homoglyphs, including twıtter[dot]com, amäzon[dot]com, and chàturbate[dot]com.
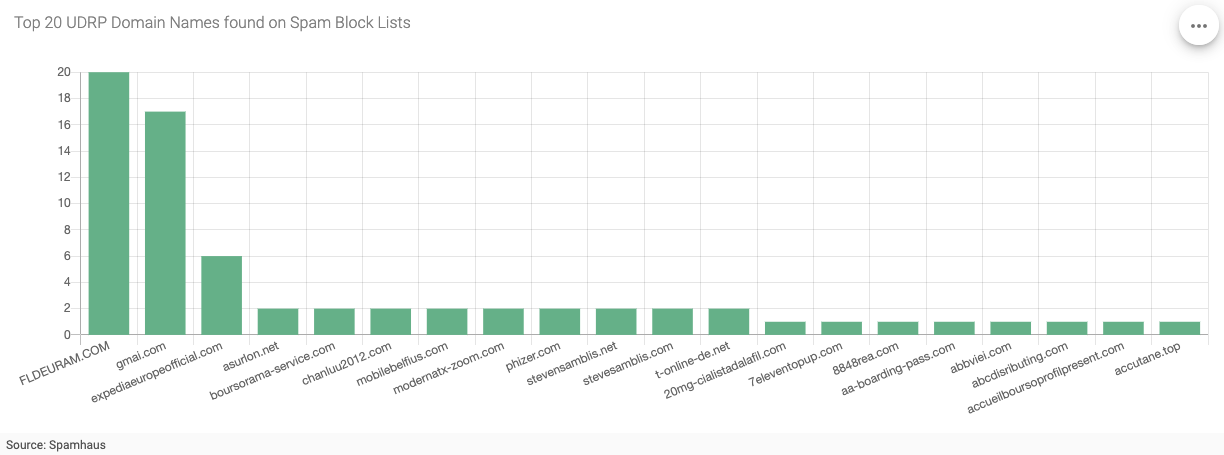
Figure 5 - Top 20 UDRP Domain Names Found on Spam Block Lists
Finally, Figure 5 (above) shows the top 20 domain names (out of 407) in the Spamhaus block list. Interestingly, we no longer see the two domain names that used Meta Platforms Inc. brands. Still, we see domain name forms typically used in spam campaigns, including typo and look-a-like domain names used to trick users into “trusting” the fraudulent email sender. E.g., gmai[dot]com, phizer[dot]com, and t-online-de[dot]net, amongst many others.
My main takeaway from this analysis is that for a small percentage of filings, the UDRP is utilized to mitigate abuse that has already been reported to industry abuse blocklists. Once again, we should ask if this is an appropriate use of the UDRP process.
Length of Decision Analysis
Finally, as mentioned above, understanding how long a typical UDRP case takes from the day it is filed to the day it is decided is key to knowing if UDRP is an appropriate tool to mitigate abuse. This is especially important given most domain names used to abuse users are active for a very short time. To prevent real harms to victims of cybercrime, immediate action is necessary to take down domains associated with malware, phishing and other crimes.
As we indicated in Part 1, determining both the filing date and the decision date is difficult to do confidently using textual analysis techniques over unstructured data. To address this issue, I again created a sample sub-set of data from WIPO for cases filed in 2023, where I am reasonably confident that these dates are good. (although not 100%). Using this sample, I can easily calculate each decision's approximate length of time.
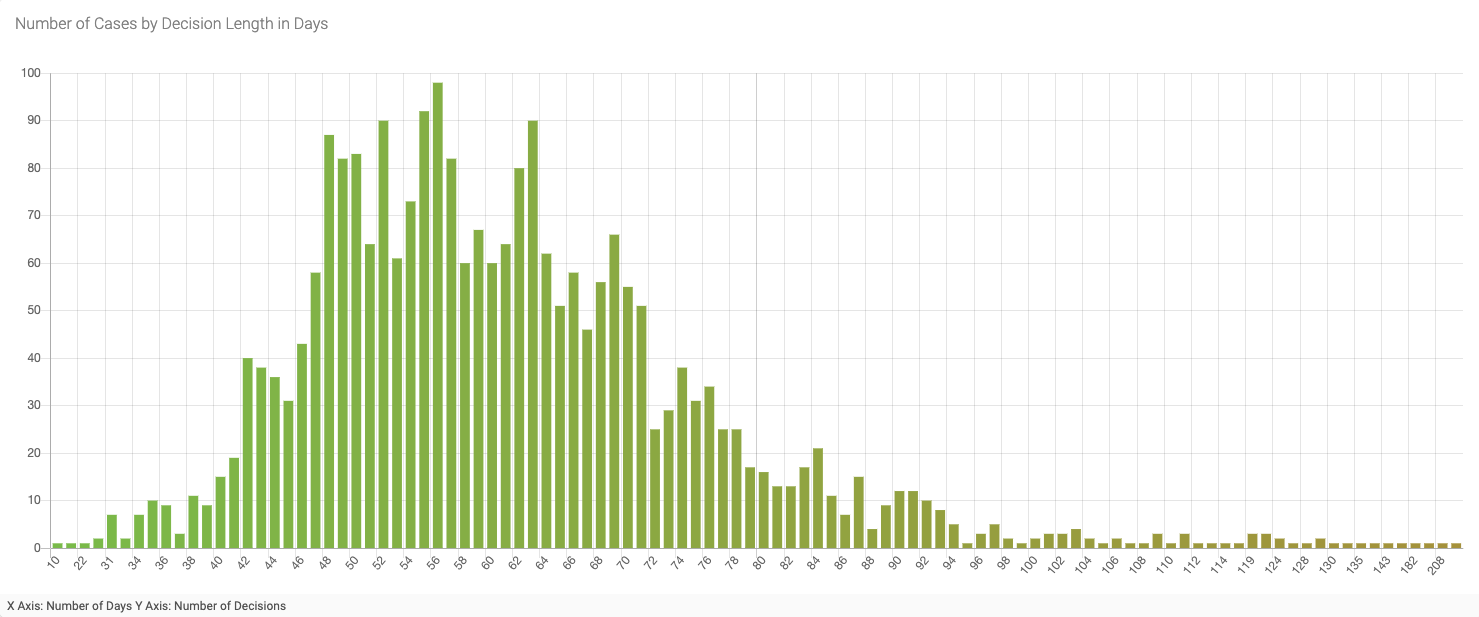
Figure 6 - Number of Cases by Decision Length in Days (Jan 1, 2023 to present)
For this sample, the shortest decision length was ten days, and the longest was 213 days. If you eliminate the outliers on the front and the “long tail” of this graph, you can see that the average number of days is roughly 60 - or two months. Interestingly, a similar distribution pattern appears when I look at the data for a longer period, e.g., from 2020, 2010, and even 2000 to the present day - including the same rough average of 60 days for cases that fall within the curve.
While 60 days seems reasonable for decisions focused on trademark disputes involving domain names and are shorter and less costly than litigation through the courts, even that short timeframe is too long to mitigate the harms of domains used for cybercrimes such as phishing and malware. The majority of domain names associated with cybercrime are only active for a few days, if not hours. However, the UDRP offers a remedy of transfer to the trademark owner, making it an attractive option if the goal is to obtain such abusive domains to ensure they can never be reregistered and reused for abuse in the future.
Key Findings
For Part 2 of our deeper dive into the DAP.LIVE UDRP data set, we looked at several aspects of the data that were not explored in Part 1. This analysis raised interesting questions about the appropriateness of using the UDRP to mitigate internet abuse, including malware, phishing, and spam. Specifically -
- Brand Representation: 66% of the top 100 most valuable brands were found in domain names referenced in UDRP decisions.
- Social Engineering Terms: The analysis of UDRP decisions also unveils the prevalence of social engineering terms within domain names. This indicates the evolving nature of online threats and unveils how UDRP can be used to mitigate them.
- Intersection with Abuse Block Lists: 705 domain names in UDRP decisions intersect with those in abuse block lists. This also indicates how UDRP is employed to mitigate abuse reported in those lists. Notably, most of the URLs reported used domain names that employed homoglyphs to impersonate well-known brands from Meta Platforms, Inc.
- Average Decision Length: The average decision length of around 60 days raises concerns about the timeliness of UDRP in mitigating the harms caused by criminal usage of domains such as phishing and malware, given the short-lived nature of their impact on users.
Finally, in an attempt to answer the question of what role the URDP should play in mitigating ever-evolving internet abuse and cyber threats, it is clear that the UDRP should have some role, especially given that abusive domain names can be “taken off the market” upon a successful complaint. However, as most harm from cyber attacks occurs within days, if not hours, the option to use mitigation methods that result in interrupting attacks much quicker than 60 days must always be considered.



