Use of Subdomain Providers Gains Popularity as a Mechanism to Launch Phishing Attacks

By Alex Deacon
Summary
How much phishing and malware abuse uses subdomain providers, versus directly registered domain names, to launch attacks against internet users? This blog seeks to answer this question using the capabilities and data feeds available in the DNS Research Federation’s DAP.LIVE platform.
36.27% of phishing attacks used subdomains from commercial providers, and the trend is going upward. Although the percentage of individual subdomain providers is low, a tiny 0.14%, these findings indicate a major governance gap in the current domain ecosystem with no multistakeholder mechanisms to bring together subdomain and hosting providers.
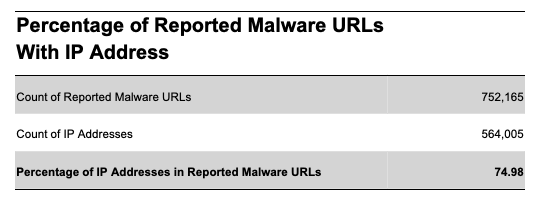
For malware, the data tells us a different story. We found that the use of subdomain providers to launch malware attacks was low, accounting for only 1.84% of the total reported URLs for the period. We believe this low percentage is because a substantial percentage of reported malware URLs, 74.98%, use IP addresses directly instead of domain names. We plan to analyze the IP addresses used in malware attacks in a future blog.
These results indicate the need for more robust and coordinated governance policies to address abuse using subdomain providers. That is, abuse happening outside the scope of the policies set and enforced by the domain name system ecosystem.
Overview
In a previous blog, “DNS as a vector for phishing attacks, different victims, different methodologies, different results”, we introduced the concept of subdomain providers. Subdomain providers are internet intermediaries that allow users to build and host internet services, sometimes for free, on shared infrastructure associated with a unique third-level domain (e.g., example-service-1.example.com).
The term ‘subdomain providers’ covers a range of services such as hosting, website, reverse proxy, and dynamic DNS. Examples include services such as duckdns.com, 000webhostapp.com, and blogspot.com, to name a few. To determine which domain names are associated with subdomain providers, we leveraged the Subdomain Provider list maintained by Maciej Korczynski of Kor Labs for the DNS Abuse Institute.
Data Feeds and Methodology
Data Feeds
For this analysis, we used the following two data feeds in the DAP.LIVE platform.
- DAP: Phishing Combined: This feed contains all the phishing URLs reported and available on both the OpenPhish and APWG phishing feeds. The data in this feed is updated once an hour, and the URLs are de-duplicated within a time window of one day (e.g. URLs reported by both providers on the same day are de-duplicated.)
- URLhaus: Complete Data Set: This feed contains all malware URLs reported to the abuse.ch URLhaus Project. The data in this feed is updated every few minutes.
Time Frame
Taking advantage of the historical data available in the DAP.LIVE platform, this analysis examined 18 full months of data from January 1, 2022, to June 30, 2023.
Methodology
To quantify abuse during this time frame, we leveraged the three measurement methodologies we defined in the previous blog, “DNS as a vector for phishing attacks, different victims, different methodologies, different results”, specifically.
- Reported URLs: The count of unique URLs reported by the abuse clearinghouses for a given period.
- Attacks: The count of “attacks” calculated by counting URLs with unique hostnames for a given period.
- Distinct/Unique Domain Names: The count of distinct/unique domain names used in phishing and malware attacks, calculated by counting unique domain names for a given period.
Phishing Analysis
Reported Phishing URLs
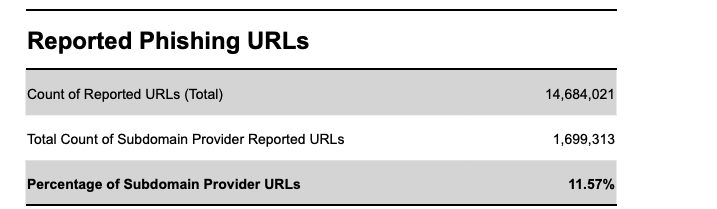
For phishing abuse during the period, we found that 11.57% of all reported phishing URLs were associated with a known subdomain provider. (Figure 1)
Figure 1- Analysis of Reported Phishing URLs
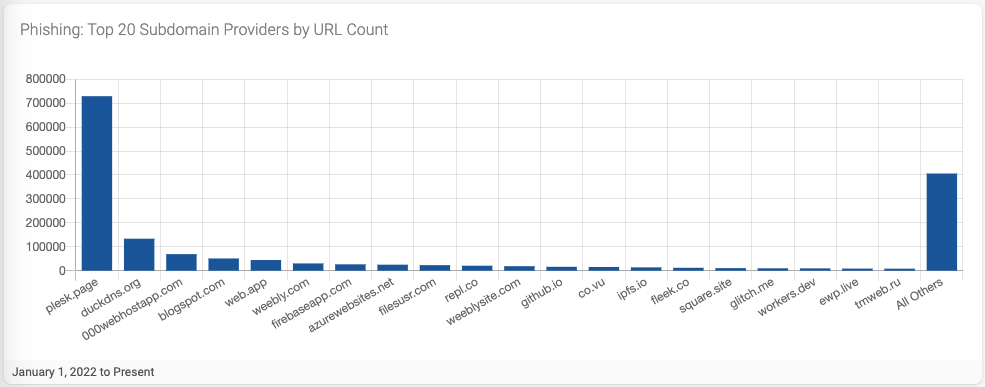
Digging deeper into the data (Figure 2), we see that plesk.page (A Swiss-based commercial hosting provider) accounts for most of the reported phishing URLs associated with a subdomain provider, followed by providers we have seen in past research, including duckdns.org, 000webhostapp.com, and blogspot.com.
Figure 2- Top 20 Subdomain Providers by Reported URL
Phishing Attacks
The monthly trend (Figure 3) for subdomain providers associated with reported phishing URLs is flat/steady, except for an enormous spike in August and September 2022. We will not investigate the reasons for this spike in this blog.
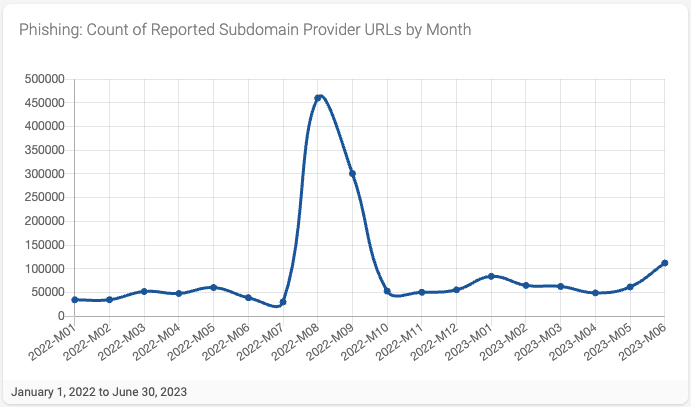
Figure 3- Top 20 Subdomain Providers by Reported URL
Analyzing the number of phishing attacks (Figure 4) gives us a slightly different view of how subdomain providers are used. Remember that measuring phishing attacks is believed by cybersecurity researchers to be the best indicator of user abuse. The data shows that 36.27%, over one-third, of all phishing attacks were launched using subdomain providers. That percentage is three times higher than the percentage for reported phishing URLs.
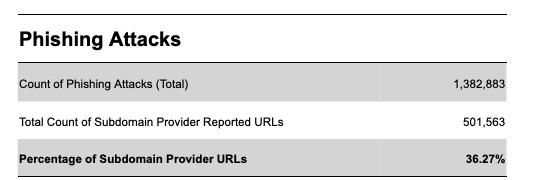
Figure 4- Phishing Attack Analysis
Interestingly, when we look at the monthly trend for phishing attacks (Figure 5), we see that the number of phishing attacks using subdomain providers is trending up, starting at a little over 20,000 in January 2022 and ending at under 70,000 in June 2023. Given this, we can confidently say that using subdomain providers is on the rise regarding phishing attacks.
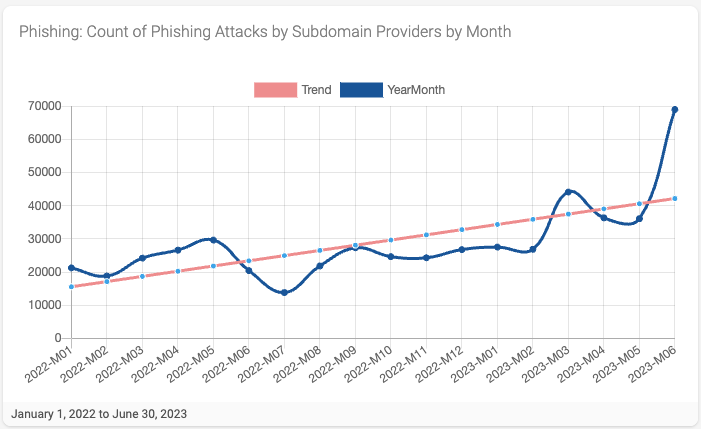
Figure 5- Count of Phishing Attacks by Subdomain Provider by Month
Distinct Domains Used for Phishing
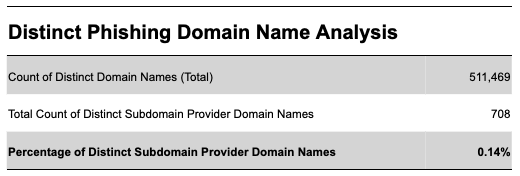
Finally, we find that the percentage of distinct subdomain provider domain names is tiny, only 0.14%, compared to the total distinct domain names we observed for the same period (Figure 6).
Figure 6 -Distinct Phishing Domain Name Analysis
While the percentage of distinct subdomain provider domain names used in phishing attacks for the period is low, only 0.14%, they account for quite a large proportion, 36.27%, of phishing attacks against users overall. This finding points to a major governance gap in the current domain ecosystem with no multistakeholder mechanisms to bring together hosting providers. The disparity between the percentages of the domain names used and the number used in phishing attacks highlights the risks of adopting a single approach to measuring the malicious use of domain names.
Malware Analysis
Reported Malware URLs
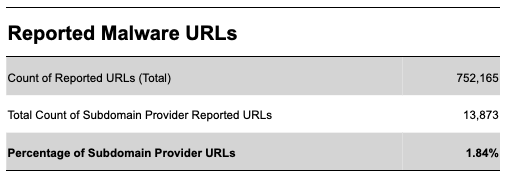
Looking at similar data for malware abuse, we find that subdomain providers are not a popular option for launching malware attacks. Only 1.84% of reported malware URLs use a known subdomain provider service. (Figure 7)
Figure 7 - Analysis of Reported Malware URLs
When we analyze the subdomain providers associated with reports of malware (Figure 8), we see a different set of providers than those associated with phishing. It is worth highlighting that the top three domains associated with reports of malware abuse are associated with major brands: live.com (Microsoft), google.com (Google), and followed closely by discordapp.com.
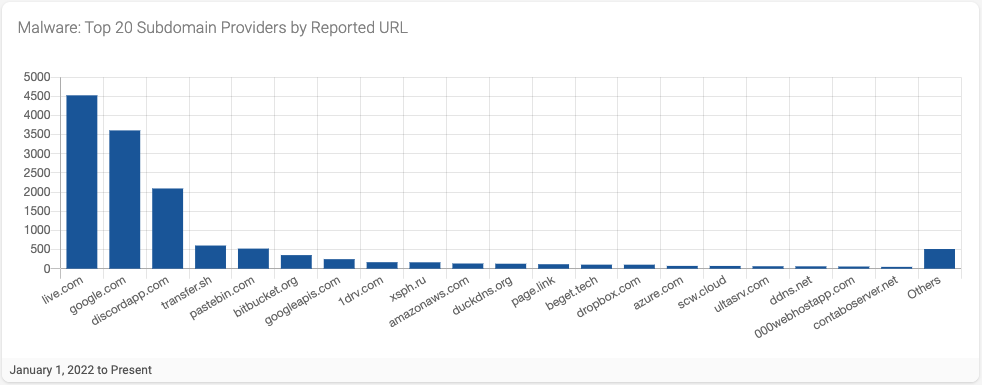
Figure 8 - Top 20 Malware Subdomain Providers by Reported URL
The monthly trend of subdomain providers associated with malware reports, while quite spikey during 2022, seems to be decreasing, starting at just about 500 reported URLs in January 2022 and ending just above 100 in June 2023. (Figure 9)
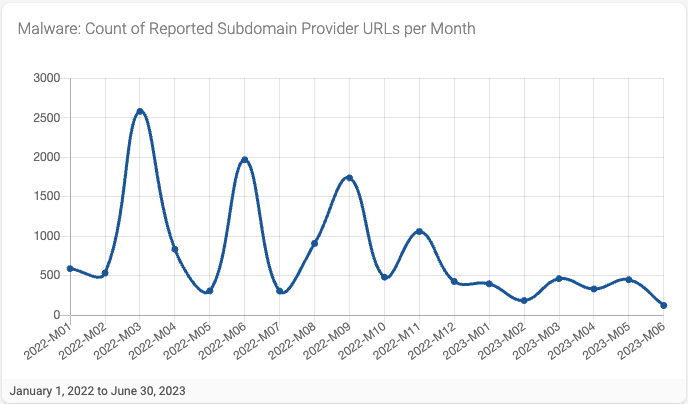
Figure 9 - Count of Reported Malware Subdomain Provider URLs per Month
Malware Attacks
Similarly, when we look at malware attacks over time, we see a general downward trend (Figure 10). In the aggregate, only 0.23% of malware attacks for the period were associated with a known subdomain provider.
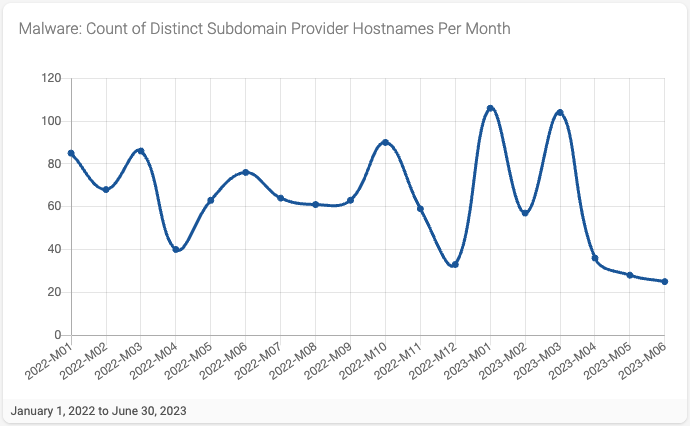
Figure 10 - Count of Malware Attacks by Subdomain Provider per Month
Unique Malware Domains
Finally, we also see a significant downward trend (Figure 11) in the count of unique subdomain providers associated with malware attacks, starting at 30 in January 2022 and dropping by 50% by June 2023, to a total of 15. In the aggregate, the percentage of distinct subdomain provider domain names used for malware is tiny, only 0.18%, compared to the total distinct domain names we observed for the same period.
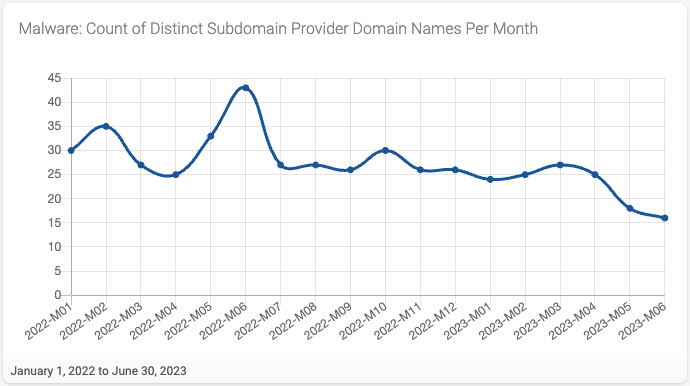
Figure 11 - Count of Distinct Subdomain Providers per Month
Is Malware abuse decreasing or just moving?
The data shows that using subdomain providers is not a popular option for those launching malware attacks on the internet and that using subdomain providers is trending down at a steep rate. To understand why this may be the case, we noticed extensive use of IP addresses (instead of domain names) in malware URLs and found that a substantial percentage of URLs, 74.98%, use IP addresses instead of domain names (Figure 12). In contrast, when we calculate the percentage of Phishing URLs, we find that a small percentage, only 2.02%, use an IP address.
Figure 12 - Percentage of Reported Malware URLs With IP Address
This extensive use of IP addresses could be why the use of subdomain providers is trending down. It could also be part of a more generalized trend that requires monitoring as cybercriminals adapt to regulatory or enhanced cybersecurity measures that apply to the domain name environment.
The use of IP addresses in malware attacks is an interesting topic for further research. We will investigate this in a future blog.
Conclusion
- More than one-third of phishing attacks use subdomain providers, and the trend is upward. The percentage of distinct subdomain provider domain names used in phishing attacks for the period is tiny, only 0.14%, suggesting that a small proportion of subdomain providers have their services exploited at a large scale by bad actors to mount phishing attacks..
- Subdomain providers are not currently popular for launching malware attacks and are trending down.
- This finding points to a major governance gap in the current domain ecosystem with no multistakeholder mechanisms to bring together hosting providers. The increasing trend of using subdomain providers for phishing and IP addresses for malware indicates the need for more robust and coordinated governance policies to address abuse using subdomain providers. That is, abuse happening outside the scope of the policies set and enforced by the domain name system ecosystem.
Notes on Methodology
- Two phishing abuse feeds (OpenPhish and APWG Phishing) and one malware abuse feed (URLhaus). The use of additional or different feeds may result in different results.
- We looked at 18 full months of data to ensure a comprehensive and historical analysis was considered.
- The Subdomain provider list was downloaded on June 17, 2023. Once again, we thank KorLabs for the use of their list.
- Our counts only indicate when a URL/domain/service provider was added to an abuse list, it does not indicate if or when the URL/site was mitigated.
- For this survey, we approximated the count of attacks using a straightforward method. Because of this, the counts of attacks in this article may not reflect the actual state or scale of attacks reported elsewhere
- The process and methodologies used have not been rigorously vetted or peer-reviewed. They are simply a means to shine a light on the data and capabilities that the DAP brings.