The .zip TLD: Ripe for abuse, but so far so good

By Alex Deacon
On May 3, 2023, Google Registry launched eight new Top Level Domains (TLDs) for public availability ( .dad, .phd, .prof, .esq, .foo, .zip, .mov and .nexus.) Since this launch, one TLD in particular - .zip - has been the focus of much debate and discussion on the dangers domains with a .zip TLD might, or might not, bring to internet users. The main concern expressed is that because .zip is a common file extension for compressed files, .zip domain names could be an effective tool to lure consumers into phishing and scams. Essentially taking advantage of the confusion between file extensions and the new .zip TLD.
Now that the TLD has been available for almost two months, we used the DNS Research Federations DAP.LIVE platform to quantify how many .zip domain names are being used in an abusive manner. Our findings show that the abuse rate for the .zip TLD is 0.20%, which is slightly below the global average of 0.22% but still quite high compared to the 0.06% abuse rate of European ccTLDs.
[Note that the same concerns exist for the .mov TLD, which shares the extension commonly used for video files; however, for this blog, we will focus only on the .zip TLD.]
.zip - file format or TLD?
Since the 1990s the .zip file format has been a popular way to compress one or more files into a single archive, suitable for storage and delivery. Over time, attackers used zip files to deliver malware and other abusive data to unsuspecting users. Because of this, the internet security community has educated users to be wary of downloading and opening files with a .zip extension from individuals they may not know. With the launch of the .zip TLD, there has been much debate around the risk and potential negative impact of domain names also ending with .zip.
Since its launch on May 3, 2023, registrations have grown slowly but steadily. As of June 19, 2023, 13,796 .zip domain names have been registered worldwide.
.zip Domain Registrations - May 1, 2023 to present
.zip domains to be malicious
To move beyond conjecture and anecdote, we wanted to leverage the capabilities of the DNS Research Federations DAP.LIVE platform to quantify how many .zip domain names have been used in active phishing, malware or spam attacks.
As of June 19, 2023 domains with a .zip extension have been found on the following abuse lists available to the DAP.
| Source | Count |
|---|---|
| Phishing: APWG and OpenPhish Lists | 7 |
| Malware: Abuse.ch URL haus | 2 |
| Spam: Spamhaus | 18 |
| Total | 27 |
Figure 2- Count of .zip domains names by source
As we know the total registrations for the .zip TLD, we can calculate a simple abuse rate by dividing the number of abusive domains by the total number of registrations.
27/13,796 = 0.20%
To put this in context we used the same algorithm to calculate the abuse rate of all TLDs in 2022. While an abuse rate of 0.20% is slightly below the global average of 0.22%, it is above the 0.06% abuse rate of the European ccTLDs and below the 0.34% abuse rate for new gTLDs.
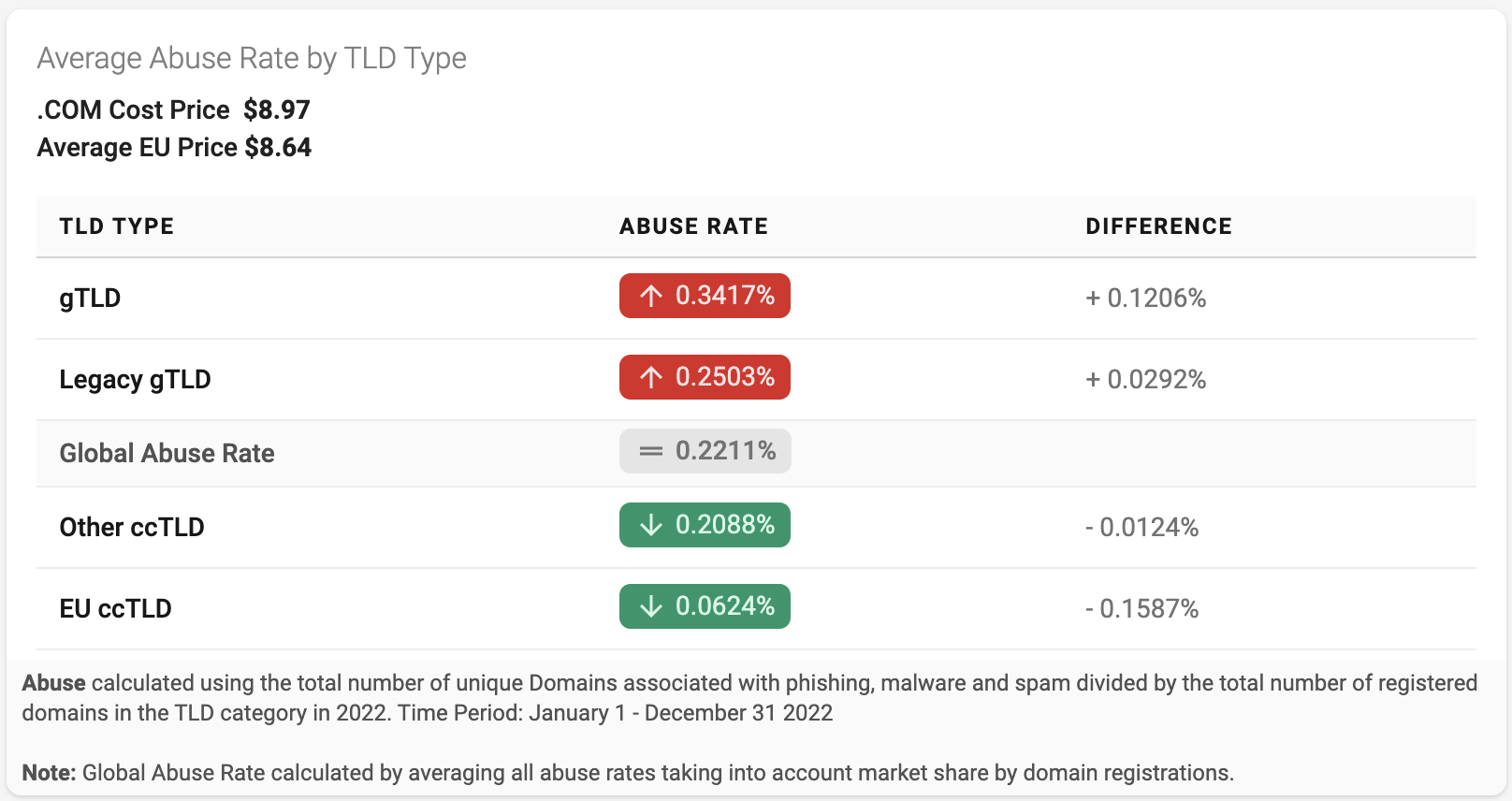
Figure 3 - Average Abuse Rates by TLD Type
Social Engineering Terms and Well-Known Brand Occurrences
One concern about the potential harm of .zip domain names is how they might be used to lure users into clicking on URLs that contain social engineering terms and even popular brands. We described how terms and brands are used as lures in the first Exploring DAP blog “Bait and switch - how social engineering terms combine with brand domains to lure users into online scams.”
Using the Zone File data made available by DAP.LIVE we can see which terms and brands have been registered. Zone files include the latest domain names registered (and deleted) for each TLD and are updated periodically by each TLD Registry Looking at the latest zone file data for .zip we found that 6.5% (892) domain names contain one of the 22 social engineering terms on our list.
Social Engineering Term Found in Domain Name - All Time
The top four terms found in .zip domain names - update, install, download and secure - are popular terms used to lure users into clicking on URLs. While It is too early to say whether these domains have been, or might be, registered or used for malicious purposes, the large percentage (6.5%) seems high and concerning.
Using a similar approach, we looked at the top 100 global brands often used by attackers to lure users into clicking on abusive links. Because Registries often provide a “sunrise period” allowing brand owners to register their trademarks before the general availability of the TLD, we focused the search on domain names registered after the May 3, 2023 launch date for the general availability phase.
Domains Counting Top 100 Brand - Registered After May 3rd Launch
After the May 3, 2023 launch date a total of 218 domain names were registered that contain one of the top 100 well-known brands, representing 1.74% of all .zip registrations.
During the sunrise period, the zone files tell us that 21 domain names associated with one of the top 100 well-known brands were registered including 15 for Google and one each for BMW, Instagram, Mercedes-Benz, Amazon, Facebook and YouTube. Sunrise periods are used by registries to allow brands to register domain names associated with their trademarks before the general availability of the TLD. However brand owners also register domain names after the sunrise period, so it is difficult to know how many of these domain names have been registered by the brand owners themselves or by someone else.
Conclusion
Our findings show that the abuse rate for the .zip TLD is 0.20% which is close to the average compared to all other TLDs. This rate indicates that .zip domain names are not being used to attack users more than the average TLDs - at least for now. However, if attackers find they have better success using .zip than other TLDs, the rates of abuse might change.
Given new TLDs, such as .zip, tend to have a higher abuse rate than legacy and ccTLDs we suggest that the security research community should continue the healthy debate about the potential risks of the .zip TLD and that internet users continue to be weary of downloading and opening files with a .zip extension or TLD from sources or individuals they may not know.
Notes on methodology
- To count the number of .zip domain names on the DAP.LIVE abuse lists we used the “distinct domain” methodology described in our list Exploring DAP blog “Blog: DNS as a vector for phishing attacks, different victims, different methodologies, different results”
- The following DAP.LIVE data sources were used in our analysis:
- DAP: Phishing Combined: This feed contains all of the Phishing URLs reported and available on both the OpenPhish and APWG phishing feeds. The data in this feed is updated once an hour and the URLs are deduplicated within a time window of one day (e.g. URLs reported by both providers on the same day are de-duplicated.)
- URLhaus: Complete Data Set: This feed contains all malware URLs reported to the abuse.ch URLhaus Project. The data in this feed is updated every few minutes.
- Spamhaus: Domain Block List: This feed contains a list of domains on Spamhaus' domain block list. It is updated once an hour.
- Zone Files: Domains: List of all available domains obtained by processing zone files from the CZDS and other ccTLD providers. Updated once a day
- The list of the Top 100 Most Valuable Brands 2022 was obtained from https://www.visualcapitalist.com/top-100-most-valuable-brands-in-2022/. For our queries, we removed the brand EY as it is a very common string found in domain names.
- The process and methodologies used in this analysis have not been rigorously defined or vetted. They are simply a means to shine a light on both the data and capabilities that the DAP brings to the table.
Appendix
.zip Domains on Phishing Lists
.zip Domains on Malware Lists
.zip Domains on Spam Lists
References
- 8 new top-level domains for dads, grads and techies | Google Blog
- New TLDs: Not Bad, Actually | Eric Lawrence - text/plain
- The Dangers of Google’s .zip TLD. Can you quickly tell which of the URLs… | by Bobbyr | May, 2023 | Medium
- The .zip gTLD: Risks and Opportunities | SANS ISC
- Zip domains, a bad idea nobody asked for | Malwarebytes Labs
- The Real Risks in Google’s New .Zip and .Mov Domains | WIRED
- Newly launched .zip already looks dodgy | Domain Incite
- Bait and switch - how social engineering terms combine with brand domains to lure users into online scams | DNS Research Federation.
- Ranked: The Top 100 Most Valuable Brands in 2022
Join the discussion
#newTLD #google


